REFLECTOR v1.0 Burp Suite extension is able to find reflected XSS on the page in real-time while browsing on the website and inclu...
REFLECTOR v1.0
Burp Suite extension is able to find reflected XSS on the page in real-time while browsing on the website and include some features as:
- Highlighting of reflection in the response tab.
- Test which symbols is allowed in this reflection.
- Analyze of reflection context.
- Content-Type whitelist.
Usage
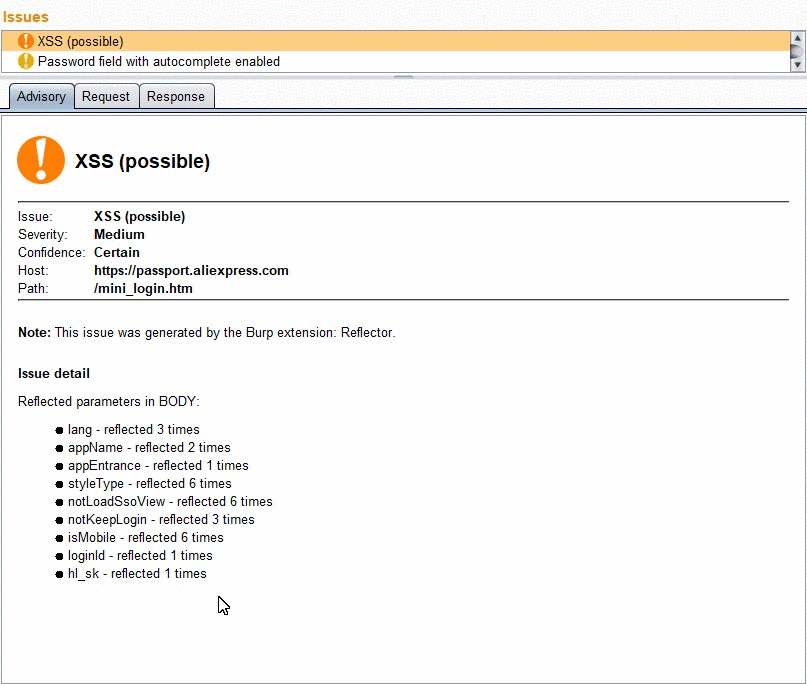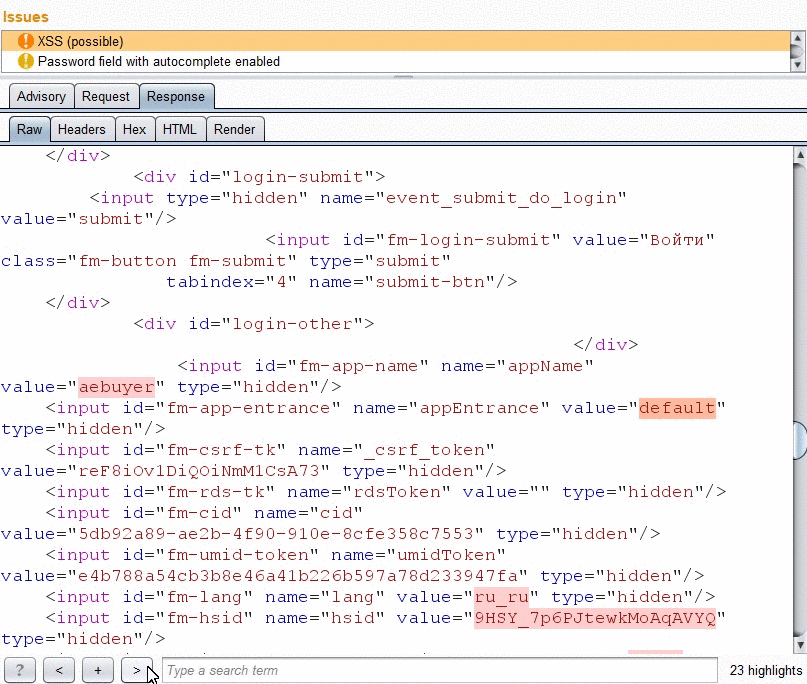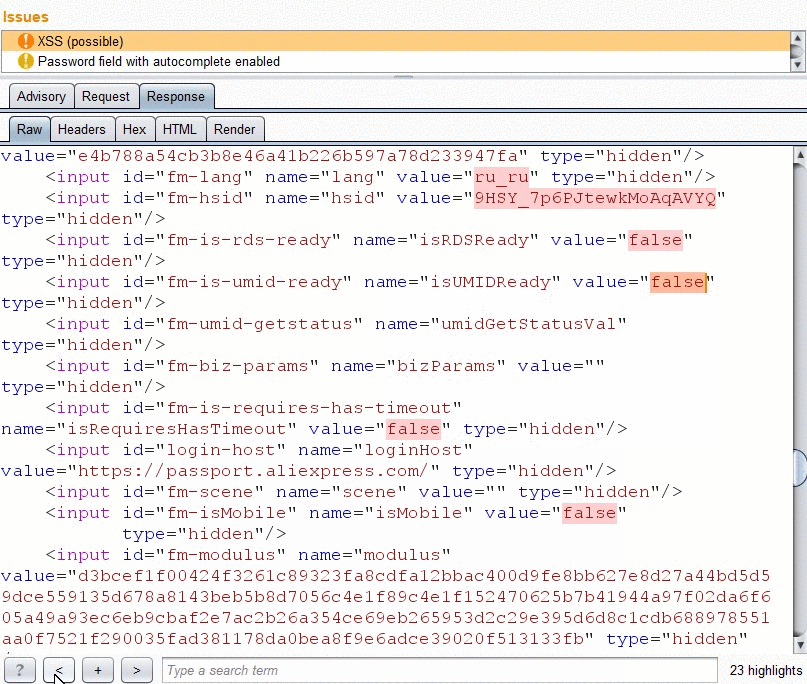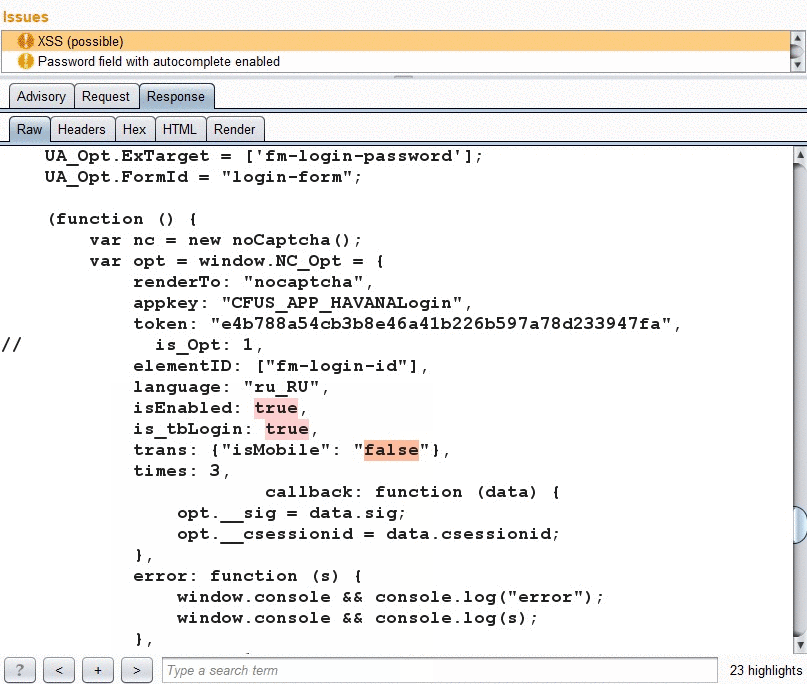
After plugin install you just need to start work with the tested web-application. Every time when reflection is found, reflector defines severity and generates burp issue. |
Each burp issue includes detailed info about the reflected parameter, such as:
- Symbols that allowed in this reflection.
- Highlighting of reflection value in response.
- Reflection context analyze.
Allowed Sybmols Analyse
Context Analyse
In the "Check context" mode reflector it does not only show special characters that are reflected the page but also figure out a character that allows breaking the syntax in the page code. In the example, you may see server response by reflector extension. Parameter "search" was sent with a payload - p@y<"'p@y. As a result, it was reflected a few times in different contexts.- reflection with next characters - ',", < and the double quote allow to exit from this context and write HTML code.
- reflection with next characters - ", < and the bracket allow to inject HTML-tags.
- reflection with next characters - ',", < and the single quote allow to exit from js variable context and write malicious code.
- Context char - a character that allows breaking the syntax.
- Other chars - other chars that are reflected without context.
Reflection Navigation
Navigation by arrow buttons in the response tab.Settings
- Scope only - allow reflector to work only with a scope added websites.
- Aggressive mode - reflector generates an additional request with a test payload.
- Check context - activate check context mode.
Moreover, you can manage content-types whitelist with which reflector plugin should work. But if you will use another type except for text/HTML, this can lead to slowdowns in work.
Respected Authors
Shvetsov AlexandrDimitrenko Egor